Blockchain was probably the most abused and misused word in 2018. Many forget that blockchain is just a specific type of distributed ledger that exist today. The word blockchain can not be applied collectively to all DLTs.
Data on a blockchain is grouped together and organised in blocks. The blocks are then linked to one another. The blockchain is distributed across and managed by peer-to-peer networks making it a distributed ledger with no central repository.
Another pattern used to build distributed ledgers is that of the Tangle. Tangle has been introduced by IOTA which is an open source distributed ledger build specifically to handle machine economy in IOT. (Internet of Things).
The Tangle provides three main advantages over blockchain mainly:
- No miners are required.
- No transaction fees are incurred.
- Very fast. The more nodes are added, the faster the network becomes.
The Tangle is based on data structure called a Direct Acyclic Graph (DAG). An acyclic graph is a graph that does not have any cycles. When you traverse the graph a node is encountered only once.
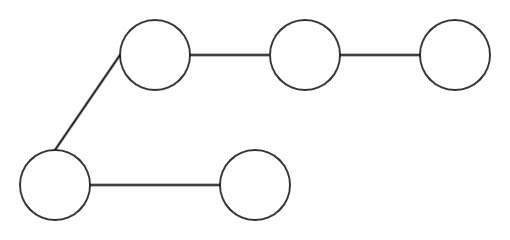
An acyclic graph becomes a directed graph ie Directed Acyclic Graph if we give edges direction.We have a data structure that moves in one direction without looping back. ie.
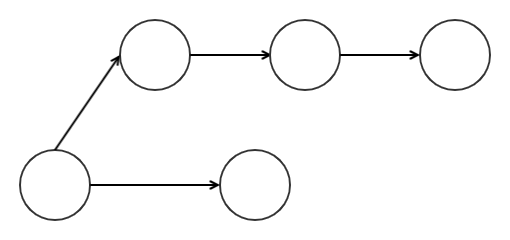
Now that we have covered the basis of what a DAG is we can dive into how the Tangle works.
In a typical blockchain like Ethereum and Bitcoin, you have two types on entities. Mainly the entity performing the transaction and the entity approve the transactions (i.e the miners). In the Tangle all the nodes validate transactions and act as a miner.
In the tangle. Each node represents a unique transaction. Nodes that have no children and called unapproved transaction tips.
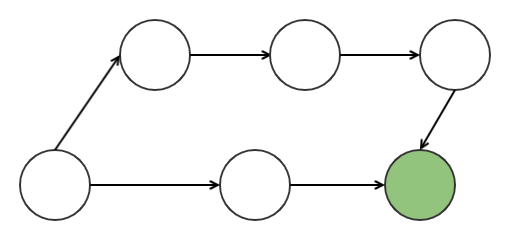
When creating a new transaction in IOTA, you must assemble two unapproved transactions tip that came before it, and attach a small proof of work to it. This results in two approved transactions and a new unapproved transaction tip.
The creation of a transaction necessitates a creation of a very small block with two other transactions on it. The proof of work is required to prevent an attacker from spamming the network. Given no group of miners are involved in the validation on the transactions there are no transactions fees.
Selection of the tips to be approved is based on a cumulative weight that is assigned to each node. The weight represent the amount of transactions that directly and indirectly references it.
The main advantage of the Tangle over the blockchain is its efficiency. In a blockchain the data the blocks are added in sequence after each other which means that transactions cannot happen in parallel. This is not the case of the Tangle as a multiple nodes can work on the Tangle at the same time. The more nodes are added the faster is the network.
This transactions efficiency and low processing power allow machine to machine payments. It allows IOT devices to be economically independent devices eg. Intelligent home appliances ordering supplies when you start to run out of items. This is only possible if the underlying infrastructure supports micro transactions at a very fast rate.
The Tangle exposes its own sets of drawbacks. Main one being that of security. A lot of people argue that given that the Proof of Work performed to validate the transaction is not hard. It makes the network un secure. As an attacker with enough hash power can overwhelm the network.
In traditional blockchain technologies, the PoW or PoS is used to elect one node that is responsible for writing data in the next block. The ”random” selection and the incentive given to a node to execute honestly the
protocol makes the whole system secure.
If you want more details about the possible security flaws in the tangle have a look at this paper. It shows how the tangle handles different attacks like the double spending attack.
For a deeper dive on the tangle you can have a look at the paper published by IOTA.
Hope you liked this article. Feel free to add me on Linkedin here or contact me on email on [email protected]


