Contact tracing with social distancing has been a core component in the measure to control the transmission of the COVID-19 transmission. In this article, I am going to cover the protocol proposed by the DP-3T consortium.
What is DP-3T ?
DP-3T is an international consortium of legal experts, epidemiologists and engineers who are developing proximity tracing standards that safeguard the fundamental rights of the user—making sure that data protection is not an afterthought however ensuring that the protocol can be used across different borders and jurisdictions.
Decentralized Approach
The standard proposed by DP-3T is based on a decentralized approach. Contact tracing is done by a mobile application. In this case a central server is only needed as a means send commands the mobile applications. Information is transmitted to the central server only in the event that an individual results to be infected with COVID-19 and the same individual gives consent for the information present on his mobile phone to be transmitted.
Technology behind the DP-3T
Following is an overview of the technology needed to implement this protocol.
Bluetooth Beacons
Bluetooth Beacons is a technology that is present in both iOS and Android Mobile Phone Platforms. This technology was aimed at the retail market. A shop can setup a Bluetooth beacon to transmit a signal to potential clients walking close to his establishment. In this case the mobile phone would interpret the signal payload and display a notification.
Bluetooth Beacons have a range of 1 -100 meters depending on the strength of the Beacon. The payload sent to the mobile phone can contain any type of data. The low power requirement used by this technology has a low impact on the battery consumption of mobile phones.
The fact that mobile phones can act as a beacon and are able to transmit and receive data is another important aspect to be noted.
Push Notifications
Push notifications is a technology present in all the major mobile platforms. It allows a server to broadcast a message to a large number of mobile phone applications. These are used by mobile apps to notify a user that an event has happened such as receiving a new message, email or a new offer. The server can bind data to the notification which can than be interpreted by the mobile app.
Contact Tracing Protocol
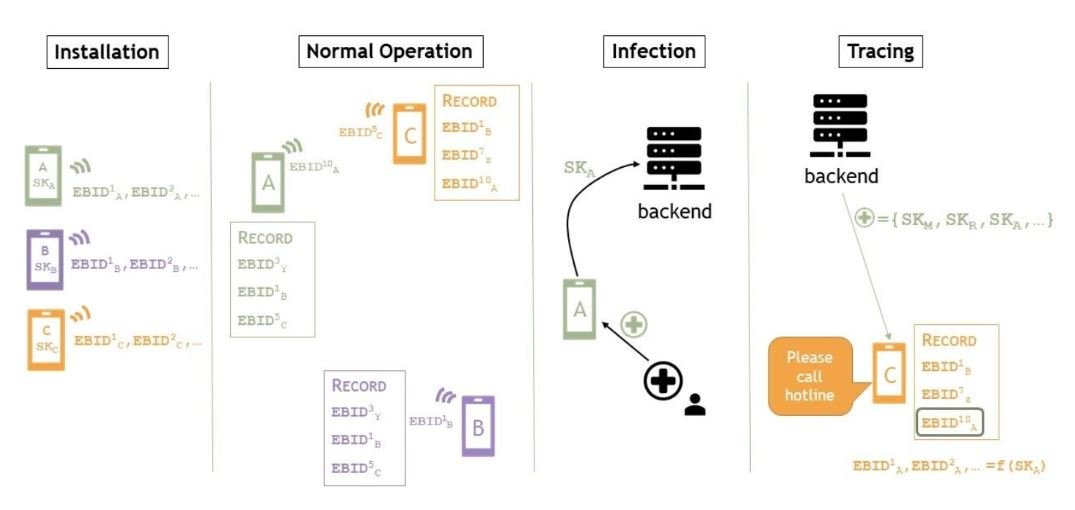
Installation
The individual installs the appropriate mobile application on his mobile phone. Once installed the mobile phone generates a secret key that is unique for each mobile device. The application uses the secret key to generate an Ephemeral Bluetooth ID (EphIDs).
Normal Operation
Each mobile phone will act as a Bluetooth beacon and transmit its Bluetooth ID. It will also record the ID’s of mobile phone devices that are in the vicinity. Over time each mobile phone will build a database of mobile phone devices that it has come in contact with.
To protect the privacy of the device. The transmitted Bluetooth ID will be changed over time. The mobile application stores the list of EphIDs used to identify the devices.
Infection
When a person is identified as positive, the health authorities will provide a unique key (token) which will authorize the mobile app to transmit the list of EphIDs that the device had been in contact with. The token will be distributed through a QR-Code. The data is transmitted to the server through a secure SSL connection.
The payload contains the token provided by the health authorities. This ensures that no bad actor can transmit information to the central server. It is important to note that the user has to provide his consent for the transmission of the data and only EphIDs are transmitted to the server.
Tracing
The server of the health authorities will send a push notification to all the devices registered. The payload will contain the EphIDs of infected individual/s. The application computes the EphIDs present in the local database and it will alert the owner of the mobile that he was in contact with somebody infected by COVID-19. He is also notified that he should contact the authorities.
Security Issues
The protocol was built with security as a core principle however there is still the possibility that a tech savvy individual can reverse engineer the application and build a version that will harvest EphIDs and identify EphIDs that have been bound to individuals that have been infected with COVID-19.
This will allow him to determine statistics of infected people in his area.
There is also a possibility of sophisticated attacks which could result in taking photos of individuals next to him and record their EphIDs. Technically this could result in determining individuals infected with COVID-19.
Final Thoughts and Considerations
Adoption of contract tracing through mobile applications can considerably reduce the amount of resources needed by governments to track quickly individuals that may be infected by the virus. This will be a game changer when countries reopen boarders. If this protocol is adopted as a standard and countries enforce mandatory installation for people crossing country boarders, it will allow easier tracking of individuals that may get infected.
The major issue with decentralized systems is scaling. It is clear that the protocol may have issues related to scale for large numbers. The protocol demands the server to send a push notification to all the devices that are registered. This will require that EphIds will be distributed between different servers and broadcasted to all the mobile phones around the different countries. Large volumes of push notifications may generate message storms which could overwhelm the push notification infrastructure of both iOS and Android.
Architecture has to be reviewed to scale to large volume of users if protocol will cover multiple countries / continents.
Hope you liked this article. Feel free to add me on Linkedin here or contact me on email on [email protected].
References
[1] https://github.com/DP-3T/documents/blob/master/DP3T%20-%20Data%20Protection%20and%20Security.pdf


